Uzone.id – As more and more businesses start to use cloud-based systems, it becomes increasingly important to have strong security measures in place. The cost-saving benefits of cloud computing, as well as its flexibility and scalability, are highly advantageous but also present many unique security challenges.
Protecting sensitive data stored in clouds requires comprehensive implementation of different best practices. Cloud computing has many advantages such as saving costs, improving efficiency, and enhancing scalability. However, these benefits come alongside several difficulties.
A McAfee report shows that 99% of cloud misconfigurations remain unnoticed by corporations thus exposing them to great risk. Moreover, under the shared responsibility model employed by most cloud providers, while they secure infrastructures users are responsible for protecting information.
How to Ensure Safety When Using Cloud Services
1) Establish Strong Access Controls
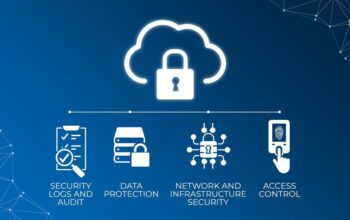
Implementing robust access controls is one of the most effective ways through which you can guarantee safety for your data within a cloud system. This may involve multi-factor authentication (MFA) or role based access control (RBAC).
MFA adds an extra layer of protection by requiring users to provide two or more verification factors before being granted entry. On the other hand RBAC ensures that individuals only possess permissions necessary for performing their duties.
“You must put into effect strict controls over who can get at what data when, where, and why if you want them protected,” said John Kindervag, Senior Vice President Palo Alto Networks.
2) Encrypt All Data
Encryption is vital for safeguarding information both while it is being transported over networks and when it’s stored in databases or other storage media within a cloud environment. With encryption applied even if an unauthorized person intercepts or accesses data, they won’t be able to read anything since it appears gibberish.
About half of all organizations surveyed by Thales indicated that they use encryption in their cloud setups although many struggle with key management.
3) Regularly Monitor and Audit Cloud Environments
Continuous monitoring together with frequent auditing of cloud platforms can help in promptly identifying and responding to security incidents. Security Information Event Management (SIEM) systems can provide real-time analysis of security alerts triggered by applications as well as network hardware.
4) Deploy a Zero Trust Security Model
According to this kind of model no user or device either inside or outside your network should be trusted automatically. Hence stringent checks must be done before granting access privileges to resources while continuously verifying what activities users are engaged in. Organizations that adopted zero trust architectures recorded 50% fewer incidences where data breaches occurred (Forrester)
5) Use CSPM Tools
These types of tools allow for easier management plus automation when dealing with security measures within cloud environments. They conduct ongoing checks on misconfigurations alongside compliance violations through continuous scanning of such aspects hence offering visibility into controls over cloud safety.
“CSPM tools play a vital role in ensuring that the cloud remains secure throughout. They do this by providing automated checks which ensure ongoing compliance as well as safety,” stated Chief Security Advisor Microsoft Azure, Lisa Lee.

Complying with Regulations and Standards
Cloud security is concerned with following rules. Some rules stipulate how information should be handled and protected like GDPR and HIPAA. Consequently, organizations need to adhere to these regulations or risk incurring heavy fines.
Data analysis: According to a Gartner study, by 2025 only 60% of companies will fulfill compliance requirements even though 80% will have moved into the cloud thus indicating a big shortfall in adhering to rules.
Ensuring data protection in cloud environments can be difficult but it is necessary nonetheless. Therefore, businesses should take various approaches simultaneously which include setting up robust access controls, encrypting data at rest or transit, watching over cloud systems continuously adopting the Zero Trust framework for network segmentation as well as deploying CSPM solutions among others that can contribute towards beefing up their overall posture on cloud safety.
Taking care of these threats early enough guarantees comprehensive utilization of cloud computing benefits while keeping critical assets secure from any harm.
“The cultural aspect of security cannot be overstated when dealing with cyber defense within any organization that utilizes this technology stack,” said Michael Johnson who works as an expert consultant specializing in Cyber Defense Systems Architecture Design (CDSAD).
To get more details about best practices for securing your data on clouds keep an eye out for industry reports and experts’ opinions on the matter.